Design Considerations
Information that will help you design and plan the implementation of 1E ITSM Connect in your organization.
This page is part of the design phase of implementation.
The implementation of 1E ITSM Connect is straightforward. Assuming you have already implemented the Tachyon infrastructure and the 1E Core App, the only significant choices required before installing 1E ITSM Connect are described below.
For a full list of requirements, please refer to Requirements. Once you have made the implementation choices below, satisfied Requirements, completed Preparation steps, then you can continue with Installing 1E ITSM Connect.
Tachyon Users and Roles
1E ITSM Connect provides ServiceNow with access to Tachyon instructions in order to ask questions about devices and run actions. It does this by using a proxy user specified in Tachyon which act on behalf of the ITSM Connect app user in ServiceNow.
You have a choice of how to configure the proxy user in Tachyon, depending on whether you want ServiceNow users to run any instruction on any device, or only have access to some instructions or some devices. Either way, your Tachyon Administrator will need to create a Tachyon user with its own domain account. This proxy user can be regarded as a service account and does not require an email address.
Within Tachyon, access to instructions and devices are permissioned using roles. The picture shows how 1E ITSM Connect app roles map to Tachyon users and their roles.
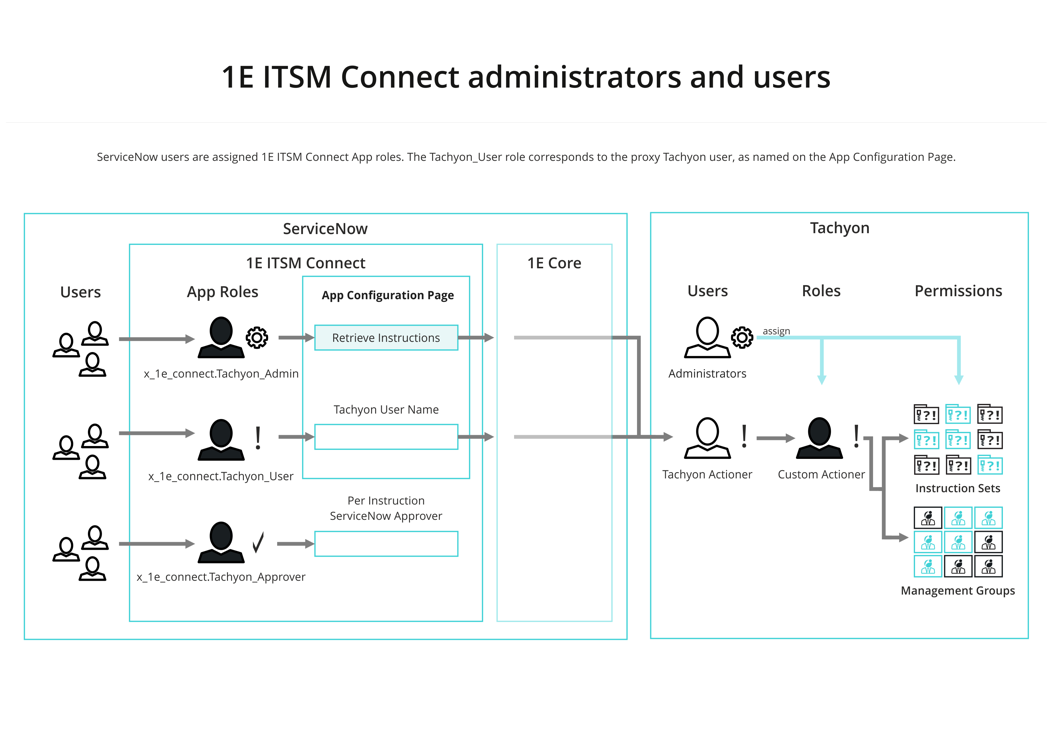
The following table describes the 1E ITSM Connect app roles.
Role name | Additional ServiceNow roles required | Description |
|---|---|---|
x_1e_connect.Tachyon_Admin | <None> | This role allows its users to configure the 1E ITSM Connect app, in addition to having the same rights as the x_1e_connect.Tachyon_User role. ServiceNow admin users must change their application scope to 1E ITSM Connect in order to configure the app, and retrieve instructions. |
x_1e_connect.Tachyon_User | ITIL (for access to ITSM incidents) | This role grants its users access to incidents and the ability to run Tachyon instructions. This role maps on to the proxy Tachyon actioner. |
x_1e_connect.Tachyon_Approver | <None> | This role allows its users to approve Tachyon instructions that require approval. |
x_1E_core_connect.user | <None> | When adding any of the above roles to a user, the x_1E_core_connect.user role is also inherited automatically. Please refer to 1E Core 2.1 - Requirements for more details. |
Instruction sets
Tachyon question and action instructions are permissioned by assigning their instructions sets to roles. You can permission the proxy roles for All sets or specific instruction sets.
You will very likely select specific instruction sets if you are using Tachyon for purposes other than ServiceNow, for example integration of Tachyon with other 1E products such as Shopping, AppClarity, NightWatchman and more.
Your Tachyon administrator will need to upload instructions into Tachyon, and assign them to instruction sets. Each instruction can be assigned to only one instruction set. Typically, instruction set names match the names of the Product Pack zips, which tend to represent their use-cases (Product Packs are available on the Tachyon Exchange and uploaded into Tachyon by an Instruction Set administrator). Users are able to see the names of instruction sets, which helps when searching for instructions to use. Therefore, you should avoid the temptation to consolidate instructions into fewer instructions sets just to simplify the one-off process of configuring roles.
Your Tachyon installation should already have some instruction sets available, with at least the Platform verification instructions used to verify the installation of Tachyon and its Agents.
Note
A Tachyon user with either Global Administrators or Instruction Set Administrators role is required to add product packs; add, modify and delete instruction sets; and delete instruction definitions.
You do not need this role if a Tachyon administrator has already added instruction definitions for you to use.
Please refer to the relevant Tachyon version documentation for how to upload instructions and manage Instruction Sets.
Management groups
Management groups are used by Tachyon as logical holders for the grouping of devices. Management groups have the following properties:
Each device known to Tachyon can be assigned to any number of management groups, or be left unassigned.
Roles can be associated with one or more specific management groups, so that users with those roles will only be available to target the devices in their role's management groups.
Management groups can only contain devices, and they are completely independent of any other management group, even if they contain the same devices.
A user with the Management Group Administrators role can create management groups in the Tachyon Portal using rules.
When creating a custom role for an instruction set, you must remember to assign one or more management groups to the role. This can be the built-in management group called All devices.
Note
A user with either Global Administrators or Management Group Administrators role is required to create, delete and update management groups.
You do not need this role if a Tachyon administrator has already created management groups for you to use.
Please refer to the relevant Tachyon version documentation for how to create and manage Management groups.
Options for configuring 1E ITSM Connect roles
Tachyon roles can be Global (system) or custom. Global roles have permissions on all instructions sets and all devices. Custom roles can be configured for all instruction sets or limited instruction sets, and all devices or management groups.
You have the following options for assigning Tachyon roles to the proxy user, which can be changed at any time.
Assign proxy user to Global Actioners role. This is the quickest and simplest option suitable as: a temporary solution which can be changed later, or in a simple environment such as a lab, or if Tachyon is used only for ServiceNow where all instructions and devices are within the scope of ServiceNow.
Assign proxy user to a custom role, for example called 1E ITSM Connect Actioner. In this case, assign role to All sets and All devices.
The same custom role as option 2, but assign the role to:
Specific instructions sets - to limit ServiceNow users to specific instructions, for example to prevent their access to system instructions
Specific management groups - to limit ServiceNow users to specific groups of devices.
Note
Please refer to:
Design Considerations to understand more about app roles, their proxy users, Tachyon roles, instruction sets and management groups
Tachyon 8.1 - The Permissions Menu for details on how to permission roles in Tachyon 8.1.
1E ITSM Connect post-installation tasks: App Configuration Page for details on how to configure proxy users in ServiceNow
User Management for information on how to set up users in ServiceNow.
Note
A user with either Global Administrators or Permissions Administrators role is required to: add or remove users; view all roles; add, modify and delete custom roles; assign roles to any instruction sets and define their permissions.
You do not need to create a role if a Tachyon administrator has already created your proxy user and assigned it to the necessary role.
Permissions Readers role can be used to review permissions in Tachyon.