Nomad architecture
A description of Nomad and its components and how they connect. The page provides a brief overview of each feature and links to other pages with more detail.
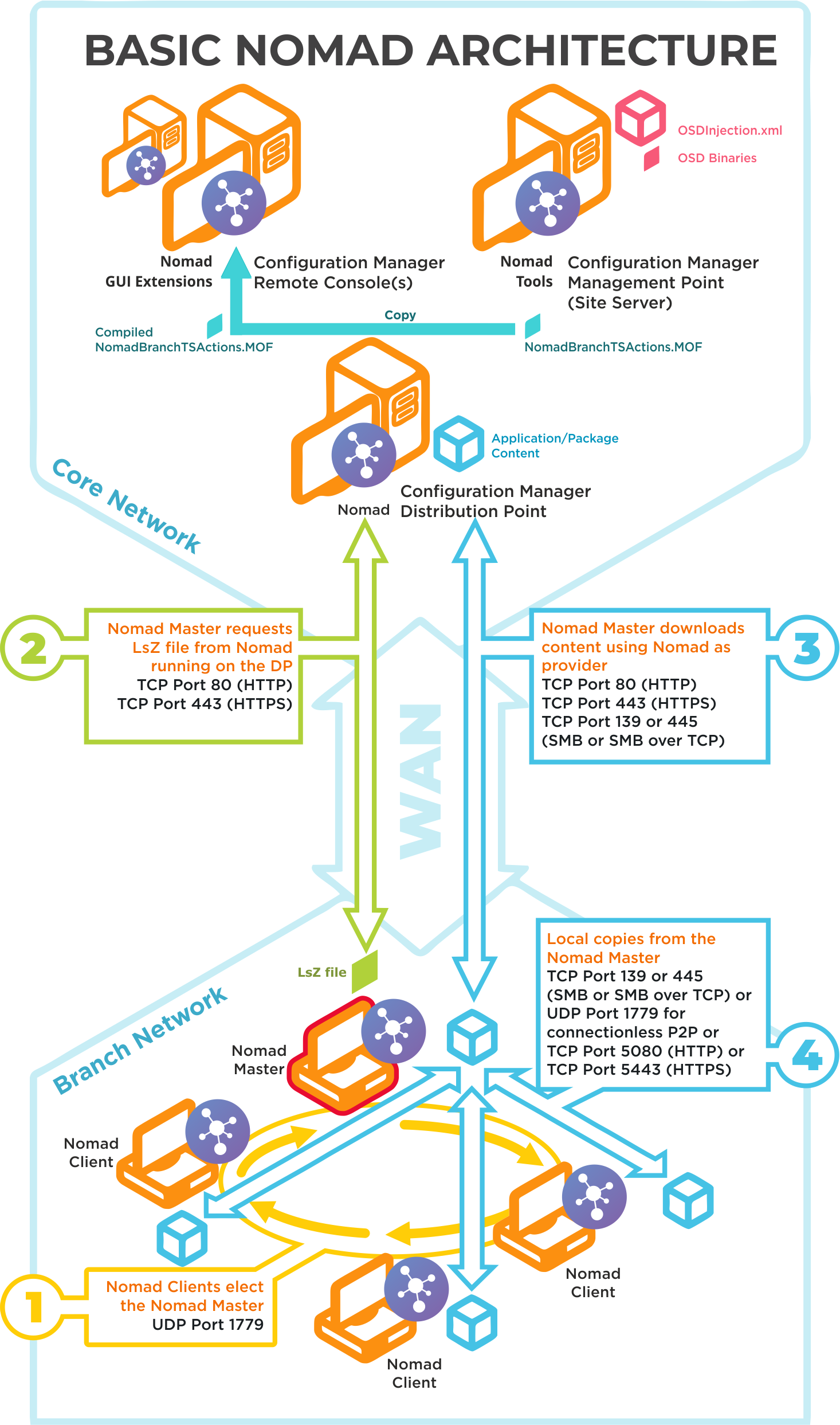
Basic Nomad architecture
Click image to enlarge.
Ports | Notes |
|---|---|
UDP 1779 | Step 1By default, Nomad uses UDP Port 1779 to communicate during the election process for determining the master on a subnet. The Nomad installer will automatically add The default value for the port may be changed at install time using the MODULE.NOMAD.P2PPORT installer property or post-installation by changing the P2P_Port registry value. If you change the default port, you must ensure all Nomad clients communicate using the same port. The Nomad port (by default UPD Port 1779) must be open on all wireless access points to facilitate Nomad peer-to-peer communications. Not all vendors enable this port by default, please refer to the specific device vendor's documentation for details on how to enable ports on each WAP device. |
TCP 80 (HTTP) TCP 443 (HTTPS) | Step 2Nomad Master requests LSZ file from Nomad running on the DP. |
TCP 80 (HTTP) TCP 443 (HTTPS) TCP 139 (SMB) TCP 445 (SMB over TCP) | Step 3Nomad Master downloads content using Nomad as provider. This communication depends on how the DP is configured. It may be one of the following:
For Configuration Manager the default setting is HTTP or HTTPS. |
TCP 139 (SMB) TCP 445 (SMB over TCP) UDP 1779 (used for connectionless P2P) TCP 5080 (HTTP) TCP 5443 (HTTPS) | Step 4Local copies from the Nomad master. The recommended way to facilitate Nomad cache access is to enable Windows File and Print Sharing. If this is not feasible on your network environment you can configure Nomad to use different means to access network shares, see Nomad cache for more details on configuring this option. Connections may use one of the following:
|
Nomad pre-caching architecture and ports
Click image to enlarge.
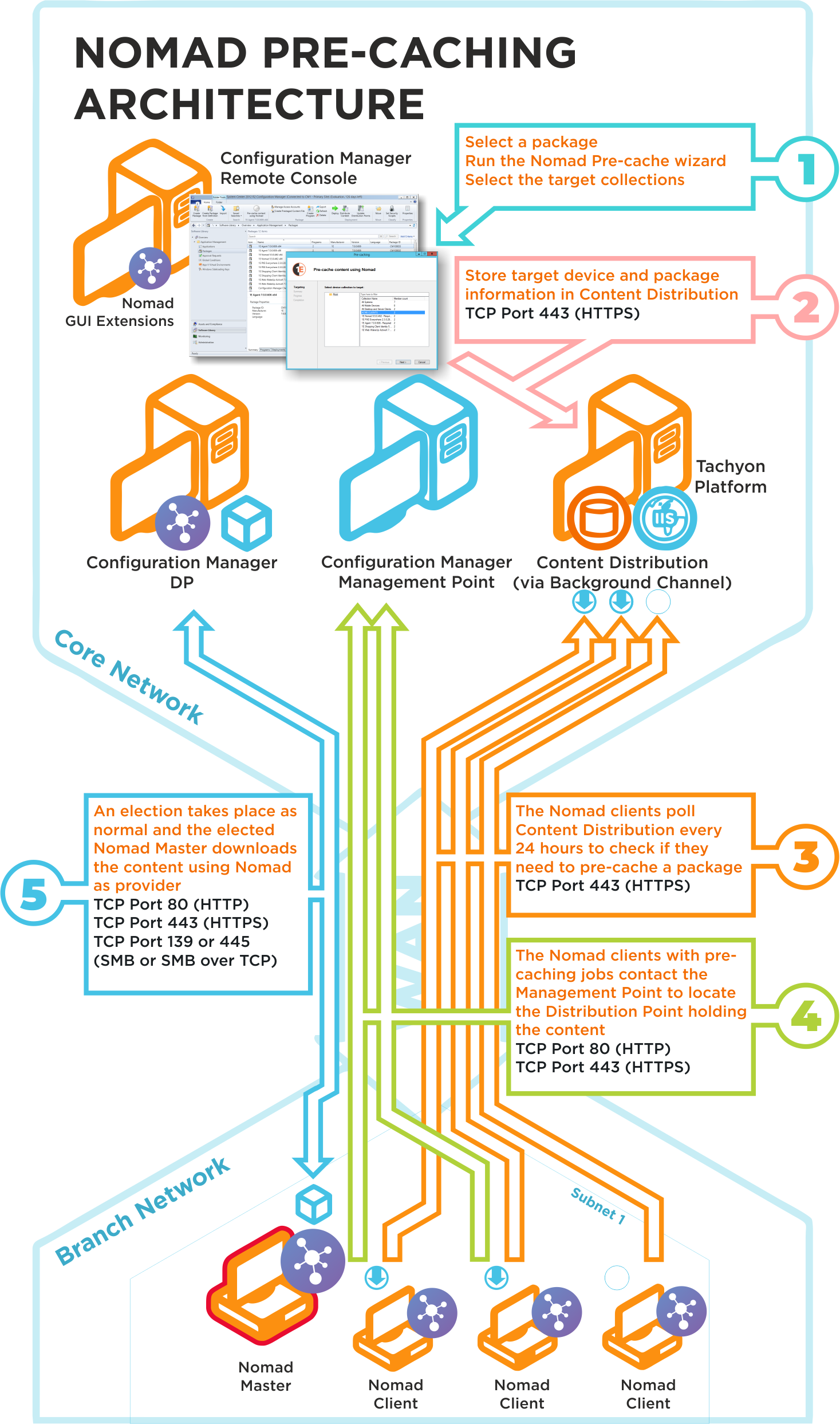
The Nomad pre-caching uses the following ports in its communications. If a site server is configured to use custom ports, pre-caching will use those ports to communicate with a management or distribution points. To ensure high-availability, pre-caching falls back to next available site server if it fails to communicate with a management or distribution point.
Ports | Description |
|---|---|
N/A | Step 1Choose a package and run the Nomad pre-caching wizard, selecting the target device collection. This step does not require any port configuration but the Nomad Configuration Manager console extensions must be installed in the Configuration Manager Console. |
TCP 80 (HTTP) TCP 443 (HTTPS) | Step 2The Nomad pre-caching wizard stores the target device and package information in Tachyon. |
TCP 80 (HTTP) TCP 443 (HTTPS) | Step 3The Nomad clients, where the pre-cache feature has been enabled, poll Tachyon every 24 hours to see if they need to pre-cache some content. This takes the form of pre-caching notifications that tell the Nomad clients they need to process a download job to fetch the specified content. |
TCP 80 (HTTP) TCP 443 (HTTPS) | Step 4The Nomad clients, with pre-caching notifications, contact the Management Point to locate the Distribution Point that holds the content. This may use HTTP or HTTPS depending on how the Management Point is configured. |
TCP 80 (HTTP) TCP 443 (HTTPS) TCP 139 (SMB) TCP 445 (SMB over TCP) | Step 5A Nomad Master election takes place and the elected master processes the job by downloading the pre-cache content using Nomad as provider. This is then distributed locally to the Nomad peers that also require the pre-cached content. This communication depends on how the DP is configured. It may be one of the following:
For Configuration Manager the default setting is either HTTP or HTTPS. |
Nomad and 1E WakeUp integration architecture and ports
Nomad integration with WakeUp enables Nomad to share content from its devices that are holding particular content, even if those devices are offline. One reason why peers in the local subnet may not respond to the request even though they have content in their caches is that they are offline (shutdown, in hibernate or sleep mode). However, if WakeUp is integrated, the Nomad client would know which offline device has the content and can wake it up when it queried Content Distribution.
The wake up list is maintained by Content Distribution and is the same list that Single Site Download (SSD) uses. Separate lists of peers are returned for subnet and site. This feature requires Nomad SSD to be enabled, Content Distribution and a NightWatchman infrastructure. The feature is enabled during installation of NightWatchman Management Center. Please refer to Nomad Preparation for requirements.
Nomad SSD architecture and ports
Click image to enlarge.
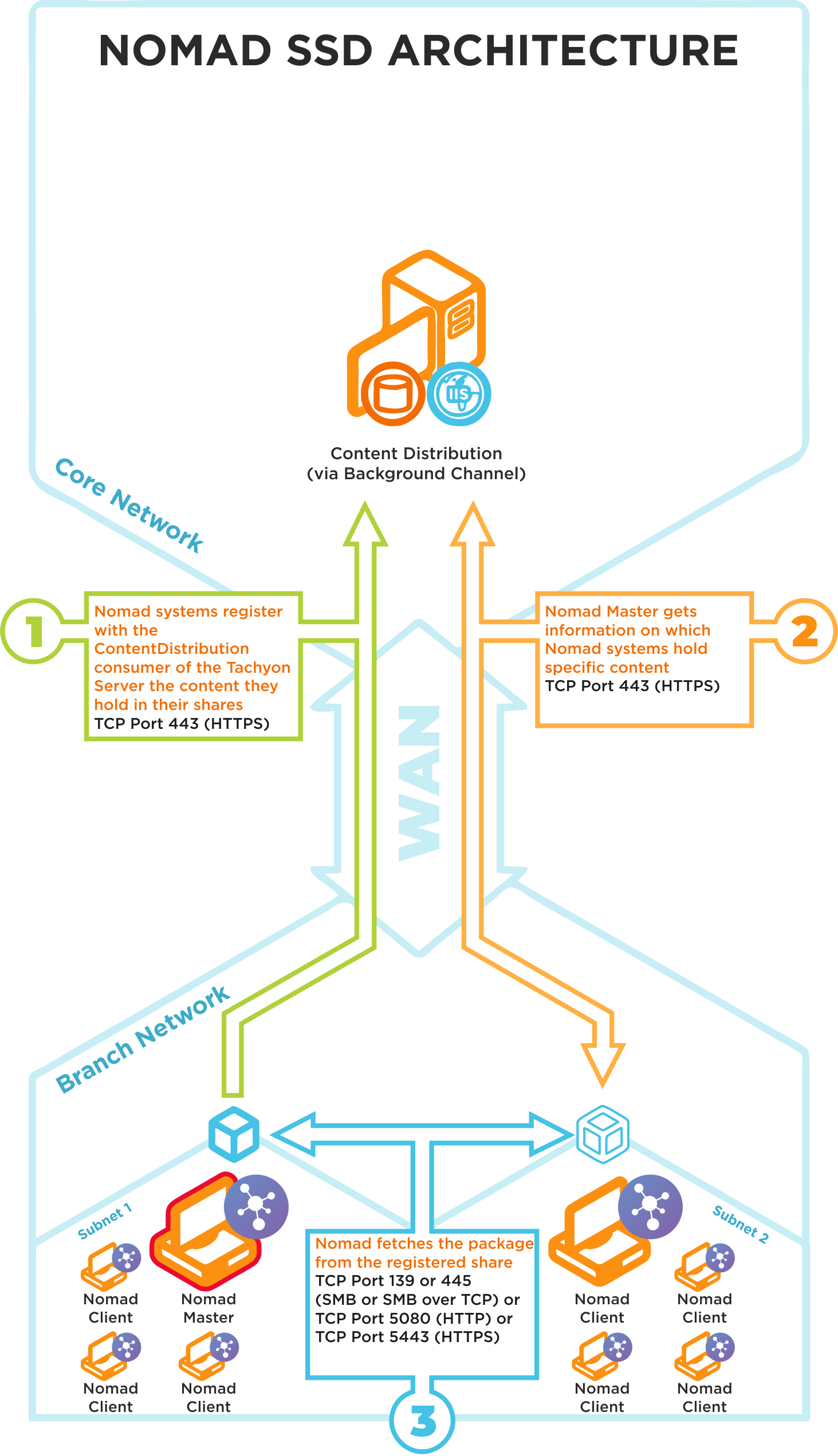
Nomad SSD uses the following ports in its communications:
Ports | Notes |
|---|---|
TCP 80 (HTTP) TCP 443 (HTTPS) | Step 1Nomad systems on the branch site register in Content Distribution the content they hold in their shares |
TCP 80 (HTTP) TCP 443 (HTTPS) | Step 2Nomad Masters get information on which Nomad systems hold specific content |
TCP 80 (HTTP) TCP 443 (HTTPS) TCP 139 (SMB) TCP 445 (SMB over TCP) | Step 3Nomad Master fetches a package from the registered Nomad share on a neighboring subnet |
We recommend that the latest version of Tachyon Platform is installed to support this feature, please refer to Requirements for more details.