Using the Tachyon PowerShell Toolkit
Guidance for using the Tachyon PowerShell Toolkit.
OSQuery integration
Using the OSQuery integration functionality available with Tachyon PowerShell Toolkit.
OSQuery is a popular open source operating system integration framework. It was originally developed by Facebook engineers and is now available as a freely reusable open source solution.
It supports Windows, Mac and Linux platforms.
Like Tachyon, it exposes operating system resources as a set of SQLite tables. There are more than a hundred tables available. Some of these overlap capabilities provided by Tachyon (such as running processes) and others provide information which augments that provided natively by Tachyon's agent.
The OSQuery integration feature lets you query any of these tables directly from PowerShell.
Please refer to https://osquery.readthedocs.io/en/latest/ for more information about OSQuery.
Getting started with OSQuery integration
OSQuery integration makes use of a Tachyon instruction, 1E-Exchange-OSQuery. This instruction has been included in the PowerShell Integration Toolkit files.
A cmdlet, Invoke-TachyonOSQuery, is then used to invoke this instruction. Before you can use the cmdlet, you must upload the instruction to Tachyon and assign it to an active instruction set.
You can either do this via the Tachyon Explorer UI or you can use the toolkit cmdlet, publish-instruction, to upload and assign the instruction.
Invoking an query on an OSQuery table
You use the invoke-tachyonosquery cmdlet to query a table with OSQuery. The syntax is:
invoke-tachyonosquery -query <query> targetscope <scope>|-targetfqdns <fqdns>
For example, we can query the table 'startup_items' as shown below.
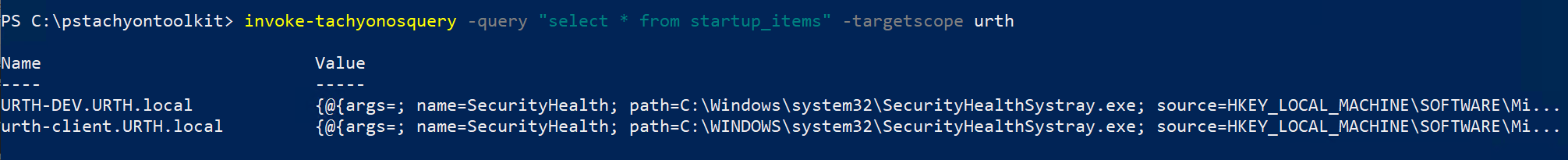 |
The invoke-tachyonosquery cmdlet returns output data in exactly the same format as other instruction invocation commands, so you can easily process it further via native PowerShell functionality.
For more information on available OSQuery tables see the online documentation at the link above.
OSQuery and forensics
OSQuery is popular with security personnel because it provides a rich variety of useful forensic detail about devices. Please refer to the following informative article that discusses using OSQuery for threat detection.
https://blog.rapid7.com/2016/05/09/introduction-to-osquery-for-threat-detection-dfir/
Under the hood
The 1E-Exchange-OSQuery instruction which is executed by the invoke-osquery cmdlet includes a copy of the OSQueryI.exe tool, packaged from a recent build of OSQuery. This is then run and the query is passed as an argument. The results, in JSON format are then passed back to Tachyon, retrieved by the cmdlet and then reformatted to match the result set that other instruction invocation cmdlets return.
The OSQueryI,.exe tool is about 13M in size. It will efficiently be distributed to devices via Nomad, ensuring that redundant copies are not sent over the corporate network. You can therefore use this functionality against any devices in your estate efficiently.