Using 1E for the first time
Signing in using your External Identity Provider
On navigating to the 1E URL, you will be presented with some additional sign in screens that integrate with your IdP.
Signing in with AAD
If your IdP is Azure Active Directory (AAD), you will be prompted with a popup similar to the one shown in the following picture.

Click on Login with Azure to continue.
You will then be prompted with the normal Azure login:
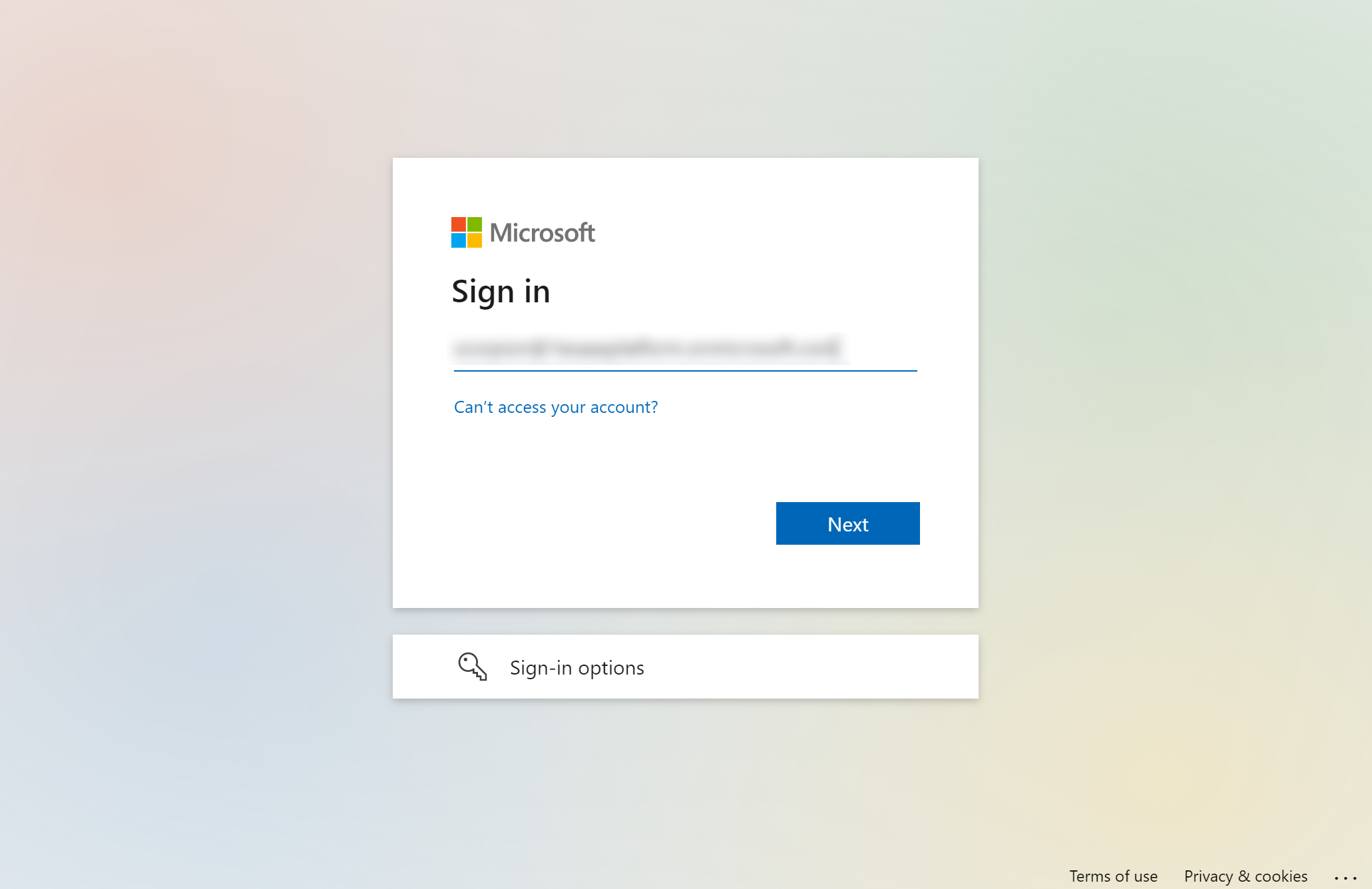
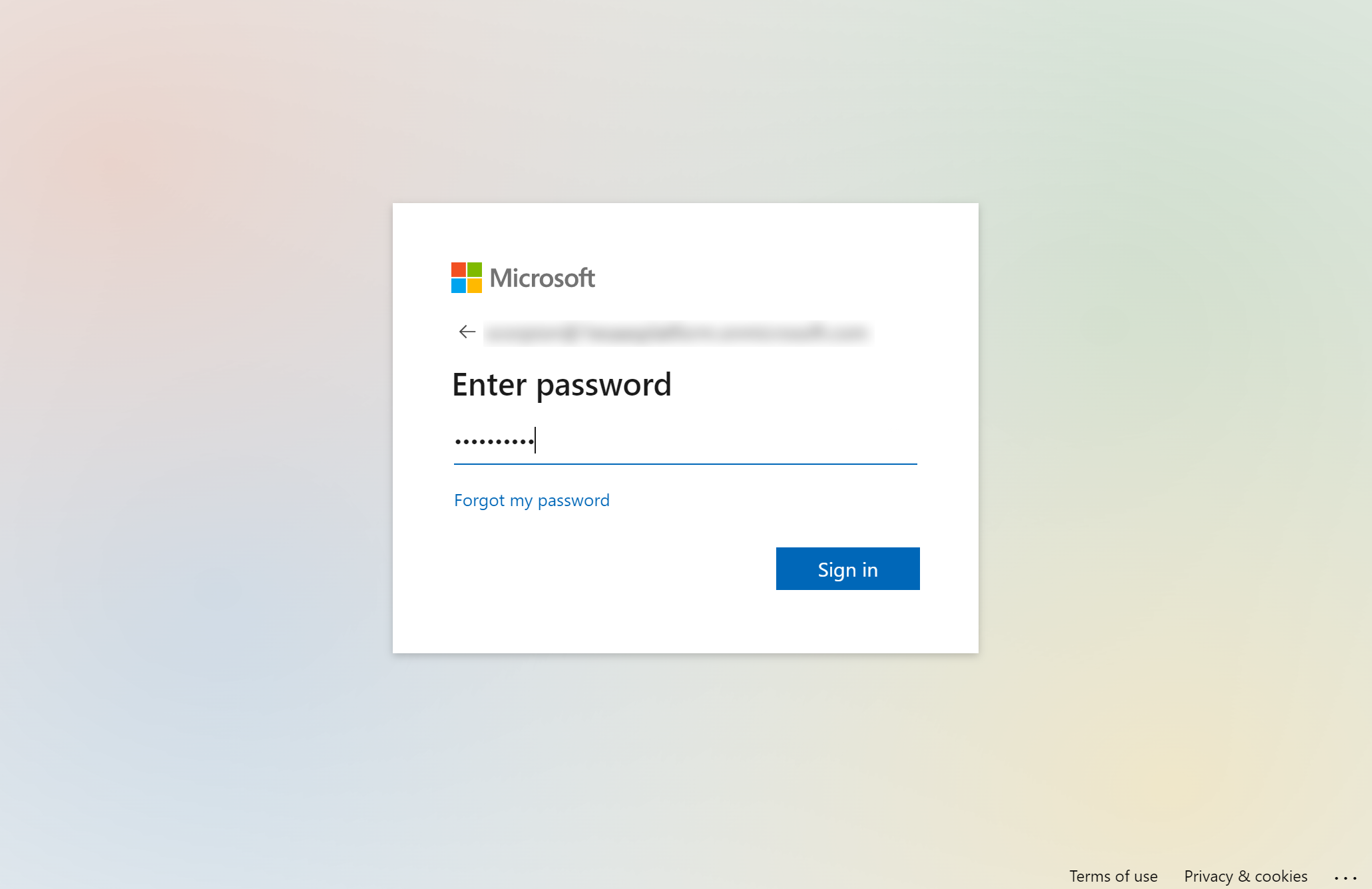
After clicking Next the Azure password dialog will be displayed.
Signing in with Okta
The sign in screen for 1E configured for use with Okta looks like this:

Click on Login with Okta to continue.
You will then be prompted with the normal Okta login asking for your username and password:
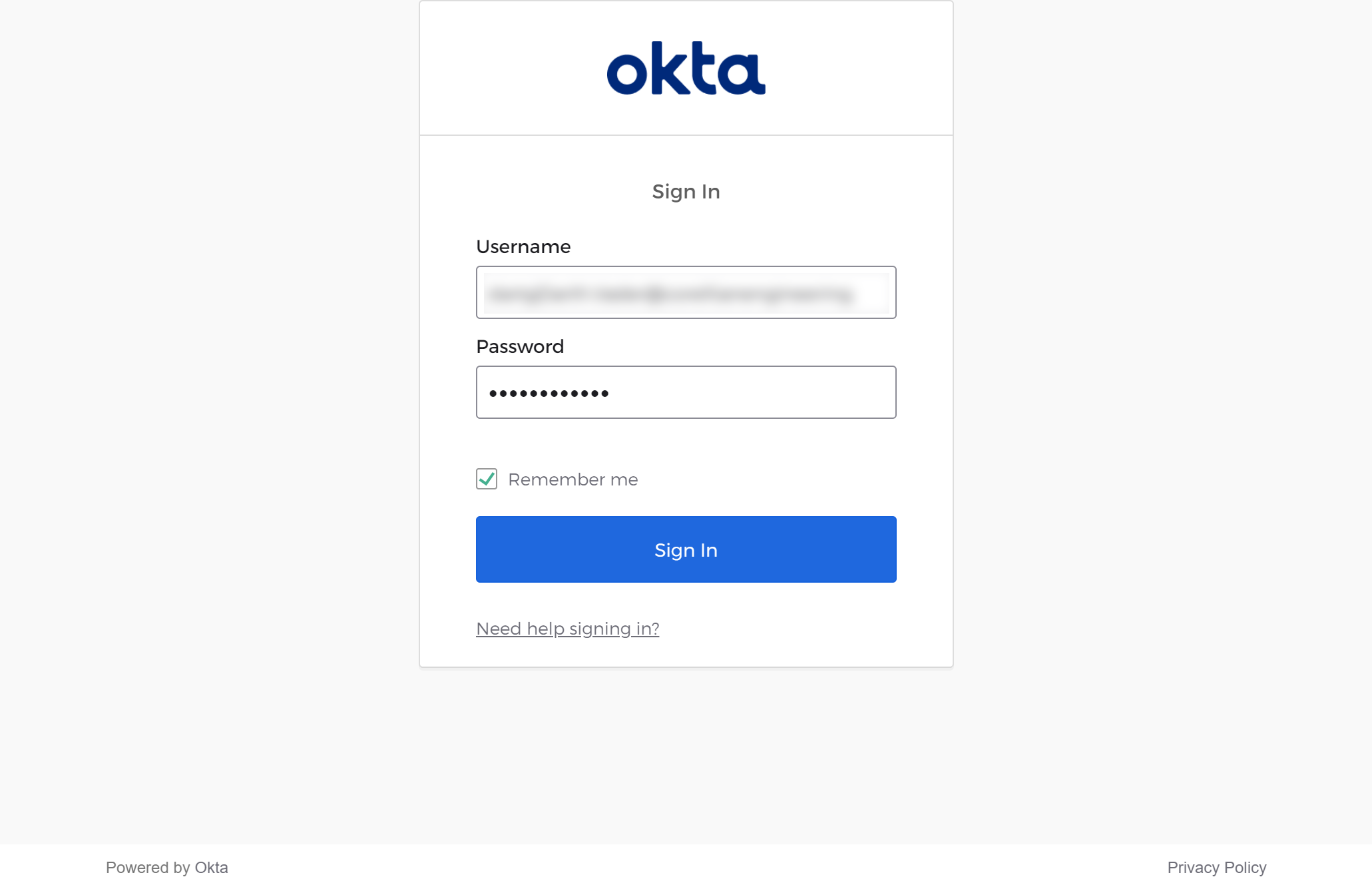
After clicking Sign In your Okta credentials will be checked and if they're ok the 1E home page will be displayed.
Accessing the 1E portal
As the Principal 1E user you will have access to all licensed applications.
From here you should navigate to Settings->Permissions->Users and Groups and start adding the Users and Groups from your IdP that you want permission in 1E. For more information, please refer to Users and Groups page.
Deploying the 1E Client
As part of the provisioning process you will have been provided with an installer command-line that installs the 1E Client for use with your 1E instance. You will need to get the correct installer for the 1E Client and deploy that to all the devices you intend to manage with 1E, using the provided command-line and the deployment tool of your choice.
As part of the Provisioning process, you will have provided to 1E a .PEM containing your organisation's Certificate Authority trust chain to help secure your 1E instance against connections from untrusted parties. 1E will only trust a 1E Client device if it presents a trusted certificate from the same CA. So any device you want to manage with 1E must have the 1E Client installed and be provisioned with a certificate from your private key infrastructure.
For detailed instructions about deploying the 1E Client refer to 1E Client.