Nomad post-installation tasks
Post-installation tasks that may be necessary to ensure that Nomad will work correctly in your environment.
You may need to make some post-installation configurations to your environment to ensure that Nomad works effectively. These areas may need attention.
Basic verification tests
For installations and upgrades:
1E Client software is installed
1E Client and Nomad Branch services both exist and running
Default path for Nomad Branch service is C:\Program Files\1E\Client\Extensibility\NomadBranch\NomadBranch.exe
System PATH environment variable has been added C:\Program Files\1E\Client\Extensibility\NomadBranch
Open a command prompt and type the following commands (Commands are in bold, example responses below):
>where nomadbranch
C:\Program Files\1E\Client\Extensibility\NomadBranch\NomadBranch.exe
>nomadbranch -version
NomadBranch version 8.1.2.xxx (mmm dd yyyy)
Nomad registry values are as expected - using default values unless specified differently in the installer, command-line or in the MST transform file
In addition, for upgrades from Nomad 6.3.201 or Tachyon Agent 4.0 - the example is for x64 but may be for x86.
1E NomadBranch x64 / 1E Tachyon Agent x64 products are uninstalled
Tachyon.Agent service is removed
System PATH environment variable has removed C:\Program Files\1E\NomadBranch\
After upgrade, the following Nomad registry settings are changed:
InstallationDirectory changed to C:\Program Files\1E\Client\Extensibility\NomadBranch
ProductVersion changed to 8.1.2.xxx
TachyonAgentVersionchanged to 8.1.2.xxx
IIS Request Filtering
By default, IIS is configured to prevent certain file types from being downloaded. You may need to configure these to allow Nomad to download all content as it does not use the Configuration Manager workaround that Microsoft had to implement to bypass its own security feature. This is done by configuring Request Filtering on each website hosting the Configuration Manager DP. The example process given below does the following:
Removes file extensions from File Name Extensions, for example .config
Removes folders from Hidden Segments, for example bin
Confirms that double escaping is enabled, to allow files with special characters in their names, for example +
Microsoft introduced IIS Request Filtering in Windows Server 2008 R2 – a security feature enabling administrators to configure IIS to block requests for specific file types and URL paths that include specific folder names or special characters. By default, IIS Request Filtering blocks a number of file extensions and folder paths that may be present in normal software distribution content (packages, applications and software updates).
Although, Microsoft's documentation highlights this issue (see link below), the Configuration Manager client bypasses this security measure by using a custom method and querying for the file rather than a standard HTTP GET for it directly. Nomad does not use the same workaround but instead adheres to Microsoft's security best-practice policy of using a standard HTTP GET for the file which is filtered out by the IIS Request Filtering feature. As a result, it is necessary to remove or configure the IIS Request Filtering feature on all distribution points to allow any file extensions, paths and special characters that may exist in your Configuration Manager content.
Note
Microsoft IIS Request Filtering for distribution points reference - https://docs.microsoft.com/en-us/previous-versions/system-center/system-center-2012-R2/gg712264(v=technet.10)?redirectedfrom=MSDN#BKMK_RequestFiltering.
Note
The following examples apply to the Default Web Site. You should only configure Request Filtering at a site level or below, not at the server level.
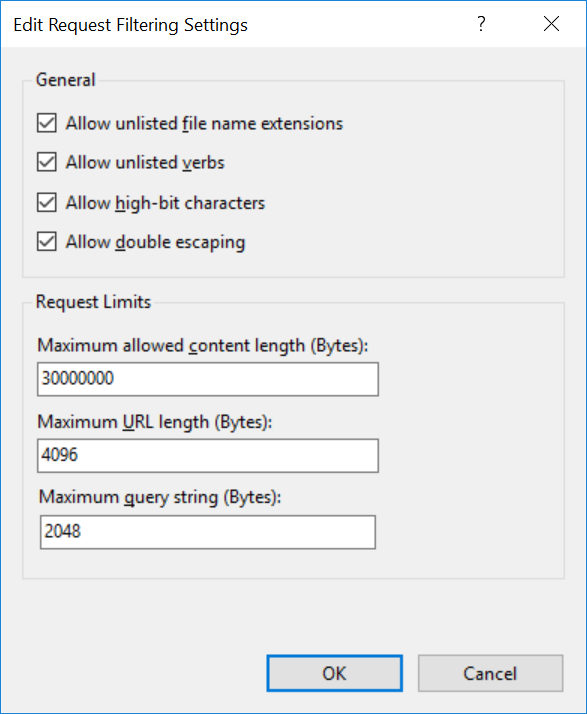
The commands also assume the Default Web Site is configured with default settings as Allow unlisted file name extensions and Allow unlisted verbs both enabled, as shown in the picture opposite.
Identifying existing restrictions
To discover files extensions and URL paths elements that are disallowed by default:
Start IIS Manager.
Locate your IIS server in the tree view and navigate to the website, for example Default Web Site.
In the right pane, double-click the Request Filtering icon (grouped under IIS).
Click the File Name Extensions tab to view a list of all the file extensions that are blocked by default. Disallowed file extensions commonly found in Configuration Manager content are:
.resources,.mdb,.config,.java,.osdx,.skin,.cs,.vbproj.Click the Hidden Segments tab to view all the folder names that are blocked by default.
In the action pane, click on Edit Feature Settings...
In the Edit Request Filtering Settings dialog confirm that Allow Double Escaping is enabled.
You can review the NomadBranch.log on clients to see details of any file types that are blocked in your download, for example:
NomadBranch.log
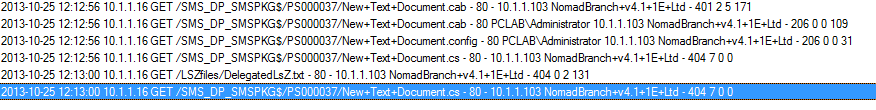
Whilst the IIS logs for the Configuration Manager distribution points serving the Nomad download requests details the blocked files types, for example a 404.7 error:
Note
Please see http://support.microsoft.com/kb/943891 for more details about HTTP status codes, for example:
404.7 - File extension denied
404.8 - Hidden namespace
404.11 - Request contains double escape sequence.
Updating the restricted list
Now that you have discovered what file types and folders are blocked by default, you can reconfigure the filtering to allow specific the file types and folders to be used by Nomad. To update the filtering:
Start a command prompt (run as administrator).
Change directory to
C:\Windows\System32\inetsrvTo remove a restricted file type, run:
appcmd set config "Default Web Site" /section:requestfiltering /-fileExtensions.[fileextension='.config']
To remove all file restrictions, run:
appcmd set config "Default Web Site" /section:requestfiltering /-fileExtensions
To change a file extension from restricted to allowed (change Allowed from false to true), run:
appcmd set config "Default Web Site" /section:requestFiltering /fileExtensions.[fileExtension='.config'].allowed:true
There is more information on restricted file types at: https://learn.microsoft.com/en-us/previous-versions/orphan-topics/ws.11/hh831621(v=ws.11)
To remove a restricted folder, run:
appcmd set config "Default Web Site" /section:requestfiltering /-hiddensegments.[segment='bin']
To remove all folder restrictions, run:
appcmd set config "Default Web Site" /section:requestfiltering /-hiddensegments
There is more information on restricted folders at: http://technet.microsoft.com/en-us/library/hh831621.aspx#HiddenSeg
By default, any path or filename that includes special escape characters are blocked. To allow filenames or paths with special characters (double escaping) to be downloaded, run:
appcmd set config "Default Web Site" /section:requestfiltering /allowdoubleescaping:true
There is more information on double escaping at: http://support.microsoft.com/kb/942076
Repeat the steps in Identifying existing restrictions to ensure that:
.configis not listed under File Name Extensionsbinis not listed under Hidden Segments
Note
It is likely that you may have to refresh the screen if IIS Manager is already open on the Request Filtering page.
Note
Alternatively, you can manually edit the web.config file for the Default Web Site normally found in C:\inetpub\wwwroot . It will contain only the differences between the Default Web Site and the Server configuration. IIS requires a restart for manual edits to take effect.
<configuration>
<system.webServer>
<security>
<requestFiltering allowDoubleEscaping="true">
<fileExtensions>
<remove fileExtension=".config" />
</fileExtensions>
<hiddenSegments>
<remove segment="bin" />
</hiddenSegments>
</requestFiltering>
</security>
</system.webServer>
</configuration>The server configuration is stored in %windir%\System32\inetsrv\config\applicationHost.config.
Antivirus exceptions
Nomad functionality may be impaired by antivirus programs, so you may also want to configure any antivirus systems running on your network to make exceptions for the Nomad executables and support files. Although we generally advise that no malware exclusions are used, it is justifiable in certain cases to isolate specific locations and files that are used by specific software. Here is a list of exclusions that could be added for Nomad, but ensure that these are compatible with any exclusions already defined for Configuration Manager before you implement them.
Nomad installed on a DP
%SystemDrive%\ProgramData\1E\NomadBranch\*.LSZ
%SystemDrive%\ProgramData\1E\NomadBranch\LogFiles\NomadBranch.log
%SystemDrive%\Program Files\1E\Client\Extensibility\NomadBranch\NomadBranch.exe
HKLM\Software\1E\NomadBranch
Nomad installed on a Configuration Manager client
%SystemDrive%\ProgramData\1E\NomadBranch\*_Cache\* (if the Configuration Manager cache is not excluded, do not exclude this)
%SystemDrive%\ProgramData\1E\NomadBranch\*.LSZ
%SystemDrive%\ProgramData\1E\NomadBranch\LogFiles\NomadBranch.log & *.lo_
%SystemDrive%\Program Files\1E\Client\Extensibility\NomadBranch\CacheCleaner.exe
%SystemDrive%\Program Files\1E\Client\Extensibility\NomadBranch\IEMNomad.exe
%SystemDrive%\Program Files\1E\Client\Extensibility\NomadBranch\NBCacheActions.exe
%SystemDrive%\Program Files\1E\Client\Extensibility\NomadBranch\NomadBranch.exe
%SystemDrive%\Program Files\1E\Client\Extensibility\NomadBranch\NomadPackageLocator.exe
%SystemDrive%\Program Files\1E\Client\Extensibility\NomadBranch\PackageStatusRequest.exe
%SystemDrive%\Program Files\1E\Client\Extensibility\NomadBranch\SMSNomad.exe
%SystemDrive%\Program Files\1E\Client\Extensibility\NomadBranch\SMSTSNomad.exe
%SystemDrive%\Program Files\1E\Client\Extensibility\NomadBranch\TSEnv2.exe
.pdb files for each executable
HKLM\Software\1E\NomadBranch