The action approval workflow
How to run actions with approval.
Running an action that restricts the number of devices sending
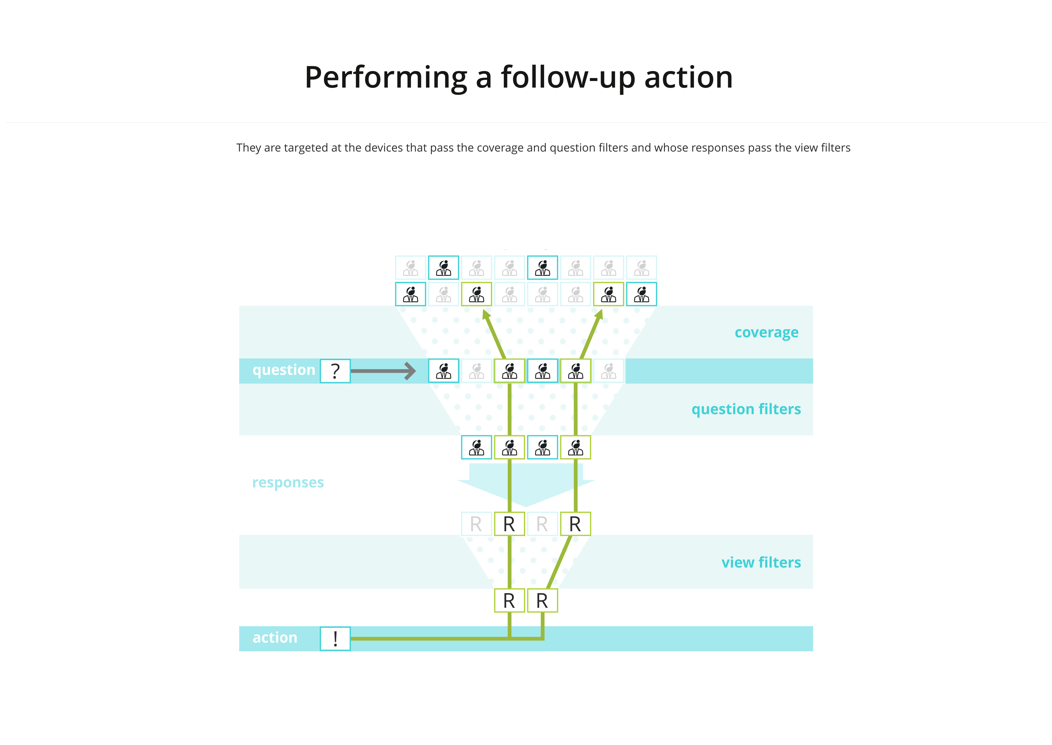
To run any action in 1E, you first need to ask a question. Questions may have coverage and question filters applied that restrict the number of devices that send responses.
When the responses come back you can apply a view filter to reduce the responses even further. When you select a follow-up action, this will be only be performed on the final set of filtered responses.
Approving an action
Configuration of approvers is explained on the Roles page.
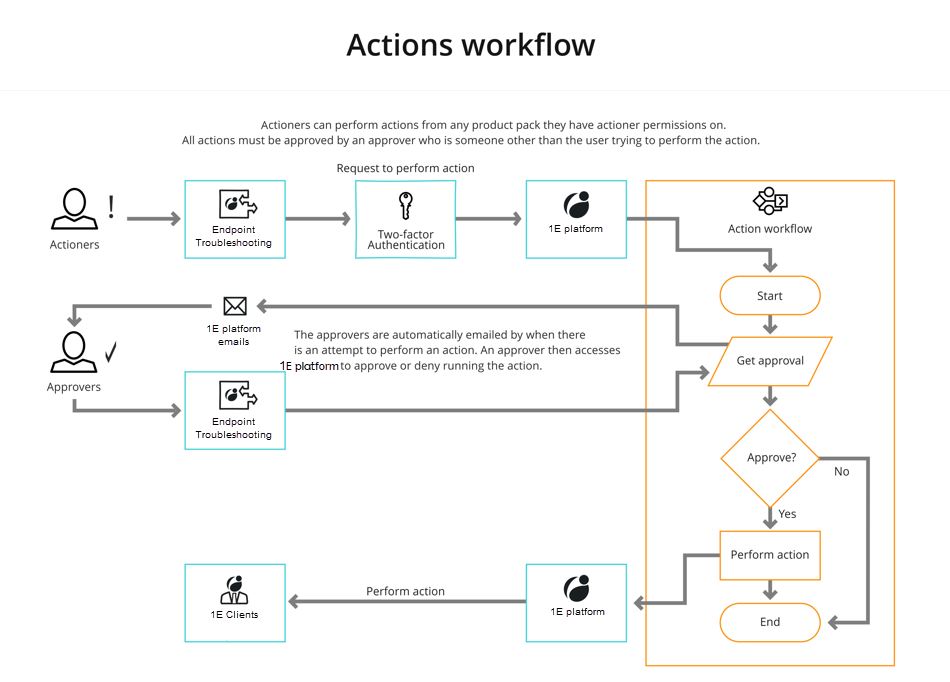
Enabling 1E platform users to run actions on devices in a network is always a powerful proposition. The potential for mistakes or deliberately malicious actions is always there. For this reason 1E platform has role-based access control to the features it presents and it implements an approval workflow that implements a process to prevent unauthorized changes from taking place.
Two-factor authentication
Two-factor authentication is now the default mode for running actions. When an actioner creates an action they are first required to enter their password. They are then required to enter an authentication code which is sent to them by email. Because this is now the default mode for performing actions there are numerous examples of two-factor authentication throughout this documentation wherever an action is described. A good example of the two-factor authentication process can be found in Performing an action - tutorial. You can also find some additional details in Two-factor authentication.
Performing an action - tutorial
A quick tutorial on asking a question and then performing an action, getting approval and confirming the action has been performed successfully.
The example
To illustrate the process of performing an action we use an example of setting registry entry for the ACMEFinance application. We do not want to create the registry entry, we only want to change an existing entry.
The ACMEFinance application has a registry entry that determines whether the automatic backup feature is enabled. We want to run a question which will find devices where the registry entry has the feature turned off and then perform a follow-up action that will turn it on for those devices.
The registry entry for ACMEFinance is under the following key: HKLM\SOFTWARE\ACME\ACMEFinance\AutoBackupEnabled
The value is a string and may be set to either TRUE, where the feature is turned on, or FALSE.
Asking a question
In this example, to perform a follow-up action we first ask a question. The responses to the question then gives 1E a list of devices to perform the action on.
In our example we want to check a specific value in the registry and change it if necessary. To find the registry related questions we enter the text registry into the Endpoint Troubleshooting and then select What is the value of registry entry <hive> <subkey> <name>?
For our example the user is TCNActioner01, with the All Instructions Actioner role, who is going to set the registry entry for the ACMEFinance application. The animation illustrates the following steps:
Type registry into the I want to field and select the What is the value of the registry entry <hive> <subkey> <name>? question.
Fill out the question variables, leaving <hive> as the default HKLM, setting <subkey> to SOFTWARE\ACME\ACMEFinance and <name> to AutoBackupEnabled
Click Ask the question and a number of responses are returned from devices where the ACMEFinance application is installed.
We are only interested in the responses where the value is FALSE. Double-clicking on the FALSE value in the responses opens up the Filter results panel with the Value set to FALSE. Cllck the Search button to filter the responses.
Now the responses show only the responses where the value for the registry key is FALSE. This filtered list represents the devices where we want to follow-up with an action to change the registry entry.
Follow-up with an action
Click the Follow-up action button.
Type registry into the edit field and then select the Set registry entry <hive> <subkey> <name> to <valuetype> <value> action from the list of matching actions.
Fill out the action variables, leaving <hive> as the default HKLM, setting <subkey> to SOFTWARE\ACME\ACMEFinance and <name> to AutoBackupEnabled. The <valuetype> variable must be set to REG_SZ to indicate a string type and lastly the <value> gets set to TRUE.
Having set and reviewed the parameters, scroll to the bottom of the page and click the Perform this action button
The action is subject to confirmation, authentication and approval. First confirm your credentials by entering the password of TCNActioner01.
When challenged to provide an authentication code, emails for TCNActioner01 are checked, and the code is copy and pasted it into the challenge dialog.
Approvers for this action are sent an email. TCNApprover01 is a global approver, receives the email, and uses the link at the bottom of the email to navigate to Endpoint Troubleshooting and approves the action.
The action runs and the responses appear to TCNActioner01. In our example TCNActioner01 sees that 1 device has had a value set.
Clicking on a response shows the device that made the response. In our example it is the ACME-WIN1001.acme.local device that has responded. This was the device that responded to the original question with the value for the registry entry as set to FALSE.
Confirm the action was successful
To confirm that the action was successful you can re-run the original question to retrieve that registry entry value.
Note
Before a follow-up action is run, all devices within the coverage will be re-asked the same question, and the 1E client will apply the filter to the latest result on each device. In this example, if someone changed the registry entry on their device from TRUE to FALSE after the first question was asked, then the filter will detect this and the follow-up action will also apply to this device.
This is why you see the Approximate target remain the same as when you asked the first question. The number of devices connected will change only if devices within the coverage come online or go offline.
Note
Using the Follow-up action button ensures the action is carried out on the filtered devices. If the Action tab is used instead then the Follow-up action applies to all the devices that were asked the question without using the filter, as if the filter has been reset.
Two-factor authentication
How 1E implements two-factor authentication for users running actions.
Two-factor authentication
1E is a powerful tool that enables changes to be made across an organization's entire estate. It employs RBAC to ensure that only users with the required permissions can run particular actions. In addition, at the point of running an action, 1E uses two-factor authentication to ensure that the logged-on user is actually the user with the correct permissions.
Two-factor authentication is implemented through a unique authentication code (one-time password) that is generated at the point of running an action. This authentication code is then sent to the user by email. The authentication code is then used to proceed with the action.