Design Considerations
What you will need to prepare in advance of implementing PXE Everywhere in your network. Typically, these are tasks that may take some time to organize, depending on how your organization works. A comprehensive list of installation and software requirements is provided in Requirements.
If you are upgrading PXE Everywhere, please review this page and then refer to Upgrading PXE Everywhere.
Network Configuration
When implementing PXE Everywhere, it must be the only PXE solution on each LAN used by your PXE clients. This means any existing PXE services on these LANs must be disabled, and any existing DHCP relays (IP helpers) that forward requests to PXE servers must also be disabled. DHCP relays (IP helpers) used for DHCP requests should be kept.
A working DHCP implementation is required. You must remove DHCP Scope Options (66, 67) you may have previously used in native Configuration Manager because they will conflict with PXE Everywhere.
By default, the Agent listens on port 67, but will listen instead on port 2067 if the Agent has been configured to run in an environment that has DHCP Snooping enabled. If Agents use a port other than 67, then support for DHCP Snooping option is assumed, and PXE Everywhere Responders must be configured to use that port. If DHCP Snooping is not being used, then Agents must use port 67, and you do not need to install Responders.
Ensure client and network firewalls are configured to support Requirements: Firewall Ports .
DHCP Snooping
One or more PXE Everywhere Responders are required when network hardware or design prevents local DHCP traffic, for example when DHCP Snooping has been enabled. Your network devices may have other settings enabled which also prevent local DHCP. Therefore, you should test your network before proceeding and determine if you can reconfigure your network and/or install Responders.
Tip
One method of testing to see if local DHCP is blocked, is to put a network packet capture tool like Wireshark on a device you intend to use as PXE Everywhere Agent, start a capture and do a DHCP release/renew from another client on the same subnet. The capture tool must be in promiscuous mode. If you can see the DHCP traffic in the packet capture, then you probably do not need a Responder. If you don’t see any DHCP traffic then you will need to consider installing Responders.
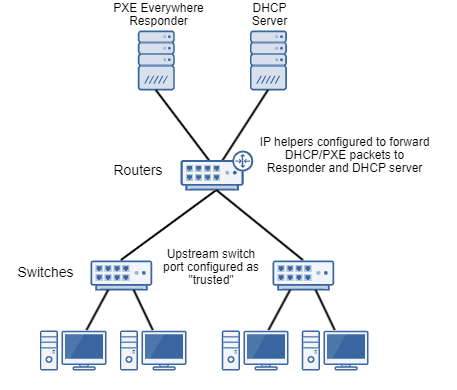
If you decide to install PXE Everywhere Responders, you will need to configure network switches to allow the PXE Everywhere Responder to receive and respond to PXE requests on port 67. Typically, this requires configuring the switch port connected to the router as "trusted". Refer to the switch manufacturer's documentation for more details.
You will also need to configure DHCP Relays (IP helpers) on routers to forward DHCP/PXE packets to the PXE Everywhere Responder(s) in addition to any DHCP Relays you already have configured for the DHCP server(s).
PXE Everywhere Agents and Responders must use a common port, which is 2067 by default. All Agents and Responders must use the same port.
Infrastructure requirements
Microsoft System Center Configuration Manager
A working Configuration Manager system is required, with clients that are healthy and functioning properly.
To test PXE Everywhere, you will need a working OS deployment task sequence and at least one remote PXE Client.
Although Configuration Manager is recommended for deploying PXE Everywhere Agent and PXE Everywhere Responder, they have no dependency on Configuration Manager itself.
You will also use a Configuration Manager Task Sequence to stage the 1E PXE Everywhere boot images on each PXE Everywhere Agent computer.
PXE Everywhere Central server
This is a web application that the PXE Everywhere Agents use to determine if a PXE client should be served a boot image. In most cases, the only infrastructure required for PXE Everywhere is the PXE Everywhere Central server, in addition to a Configuration Manager site with at least one Distribution Point. During installation, the PXE Everywhere Central installer adds some stored procedures to the Configuration Manager database that are executed by the web application when requested by PXE Everywhere Agents. In a multi-site hierarchy, the PXE Everywhere Central server should be connected to the CAS database server.
You will need to decide where to install it. You can install PXE Everywhere Central on a Configuration Manager site server, or on any other server that has IIS installed and has good connectivity to the Configuration Manager database, ideally equivalent to the connection that the site server has to its database. Suitable alternatives for hosting PXE Everywhere Central are ActiveEfficiency or Tachyon Platform server. By default, the PXE Everywhere web application will install under any website that has an HTTP binding using port 80. If there is more than one HTTP 80 binding, it will install under the first according to IIS Site order, which is Default Web Site, by default.
Please refer to Requirements for specific system requirements for the PXE Everywhere Central server, including Windows Server roles and features and Firewall Ports.
PXE Everywhere Agent
PXE Everywhere client provides a lightweight PXE server that responds to PXE boot requests from the local subnet and serves boot files to requesting PXE clients. It must therefore be installed on at least one client in each subnet where PXE booting is required, and preferably installed on all PCs in your environment, thereby providing maximum availability (redundancy) and scalability (load-balancing) for PXE boot requests.
To install PXE Everywhere Agent, you require the following:
At least 2MB of free disk space for the application, plus whatever size your boot images require (typically 130MB each).
Ensure client side firewalls have exceptions for the ports required by PXE Everywhere.
When upgrading, we recommend you update all versions of PXE Everywhere Agent running on a single subnet at the same time.
Refer to Requirements for other specific system requirements for the PXE Everywhere Agent.
For PXE clients to PXE boot into Windows PE, each PXE Everywhere Agent requires a boot image and supporting files. As this is a complex process, 1E recommends using Introducing Client Deployment Assistant to configure and simultaneously deploy PXE Everywhere Agent with the boot image. CDA integrates with Configuration Manager to create packages and deployments. If you need to deploy boot images separately they are available in the Microsoft Windows Automated Deployment Kit (ADK) as described in Preparing and deploying 1E PXE Everywhere boot images.
Note
The PXE Everywhere Agent client module in 1E Client 5.1 and later does not require a license key. PXE Everywhere 4.0 does not require input of a license key, or relicencing when upgrading or updating. Customers are legally bound to use the software within the terms of the 1E software license agreement.
PXE clients
PXE clients are computers that will PXE boot into Windows PE and install or repair the Windows OS. They do not require PXE Everywhere to be installed on them.
The following are required for clients that need to PXE boot in order to install an operating system:
PXE must be enabled in the firmware settings. Refer to the hardware-specific documentation for details on how to enable PXE. You can also use the BIOS TO UEFI tool to enable UEFI PXE on Dell, Lenovo and HP systems in a Task Sequence.
Minimum hardware specification as required by the target operating system.
LAN connection 100Mbps or greater.
PXE Everywhere Responder
As described in DHCP Snooping above, if local DHCP traffic is blocked, for example by DHCP Snooping being enabled on your network switches, then you will need to implement at least one authorized PXE Everywhere Responder, preferably on a Server OS, and enable DHCP Snooping mode on Agents. Refer to Network Configuration above for additional network configuration required to support DHCP Snooping.
The Responder can be installed on a workstation OS, however for production environments it should be installed on a server OS, as all DHCP and PXE requests will be routed to this server (in addition to your existing DHCP servers). The Responder will simply discard DHCP requests and only process PXE requests. The Responder cannot be installed on an existing DHCP server.
Note
PXE Everywhere Responder cannot co-exist on the same computer as PXE Everywhere Agent, and are not supported together. Whilst it is possible to install them together, they will not work and will have issues such as failure to bind to ports.
If you install 1E Client on the same computer then you must disable the client module for PXE Everywhere Agent. You can do this by adding
In most cases a single Responder will be sufficient. In larger environments, or environments where networks in different regions are managed by different parties, you can implement multiple PXE Everywhere Responders, each one managing different segments of your network. For example, you may choose to implement a Responder for each geographic region. This decision will often depend on your current network topology and how the network is currently managed.
To install PXE Everywhere Responder you require the following:
PXE Everywhere Responder is 64-bit only. A server OS is recommended.
Requires at least 2MB free disk space for the application
Ensure client side firewalls have exceptions for the ports required by PXE Everywhere.
When upgrading, we recommend you update all versions of PXE Everywhere Agent running on a single subnet at the same time.
Refer to Requirements for other specific system requirements for the PXE Everywhere Responder.
When implementing PXE Everywhere in a network that has DHCP Snooping enabled, you will need to use and enable communication on custom UDP ports to allow the PXE client to communicate with the PXE Everywhere agents (the standard ports are blocked by the DHCP Snooping feature). By default, the custom UDP ports used in the initial boot loader served by the Responder are set to 2067 and 2068. To use different ports you must create the following registry values inHKLM\Software\Wow6432Node\1E\PXELiteServer on Responders, and ensure that the value of AltPxeServerPort is the same as used by DhcpPort on PXE Everywhere Agents. Do not change the value of DhcpPort on Responders.
Name | Type | Notes |
|---|---|---|
AltPxeServerPort | REG_DWORD | This is the UDP port that the alternate boot loader will broadcast the custom PXE request on. The PXE Everywhere Agents must be configured to listen on this port, so it must be the same port defined by DHCPPORT when installing the PXE Everywhere Agent. If this registry setting does not exist then port 2067 is used. |
AltPxeClientPort | REG_DWORD | This is the UDP port that the PXE Everywhere Responder will reply to the PXE client (alternate boot loader) on. If this registry setting does not exist then port 2068 is used. |
Note
The PXE Everywhere Responder does not require a license key. PXE Everywhere 4.0 does not require input of a license key, or relicencing when upgrading or updating. Customers are legally bound to use the software within the terms of the 1E software license agreement.