Roles page
The Roles page lets you view system roles and currently defined custom roles. From here you can edit Role permissions and go into each role to set its users and group assignments and any associated management groups.
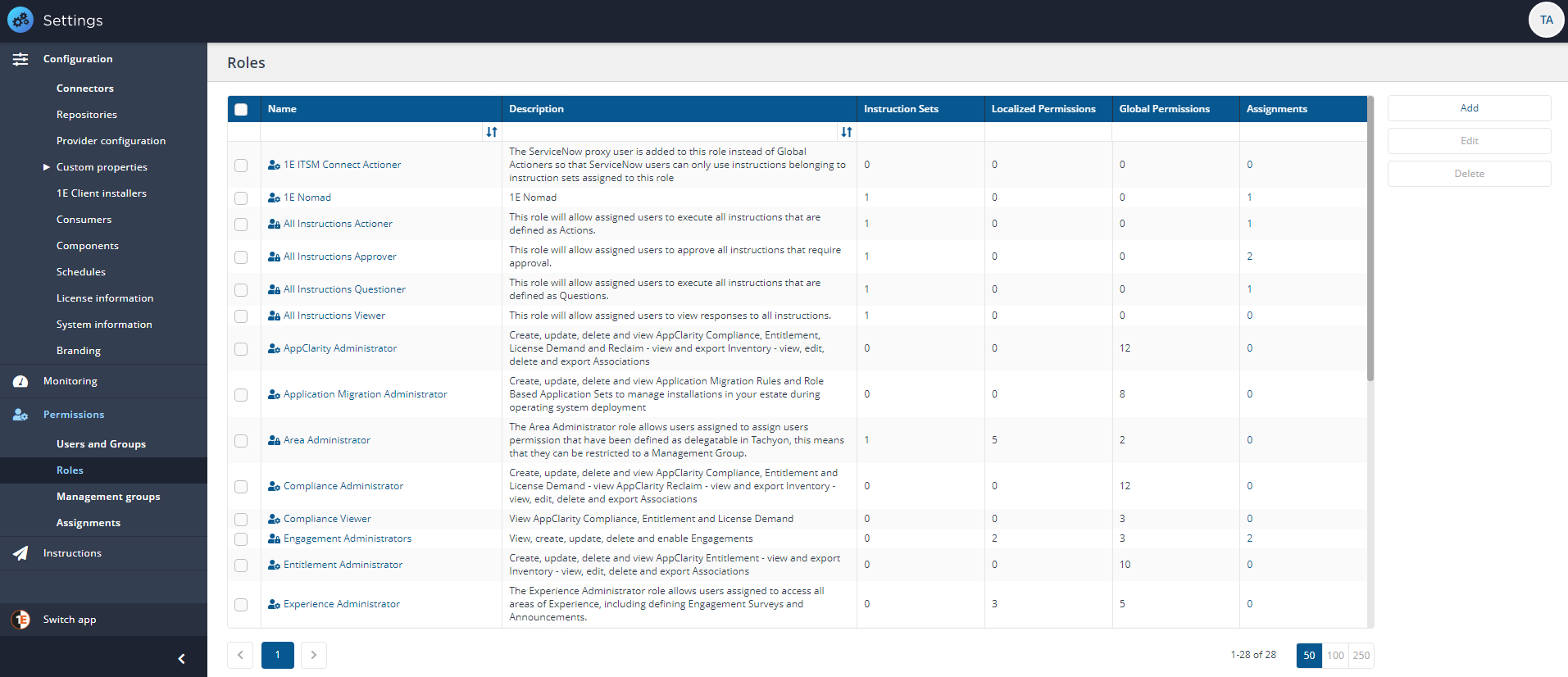
Tachyon roles
There are two types of roles that can be applied to the Tachyon users, system roles, and custom roles.
Tip
On the Roles page, you can see at a glance which Tachyon roles are system or custom roles, by using the icon in the Name column:
System roles are indicated by an icon with a padlock

Custom roles are indicated by an icon with a cog wheel

System and custom roles
Refer to Roles and Securables for a complete reference for the following:
Platform system roles.
The custom roles used by 1E applications.
For customers upgrading from Tachyon Platform 5.2 or earlier, a list of role names that are automatically renamed.
Recommendations for using the Full Administrator role
The Full Administrator role can be used to provide across-the-board permissions to a user. While this may be convenient in certain circumstances, you should be aware that this is a powerful role and should be used with appropriate caution.
Using Full Administrator in a lab environment
To get things up and running quickly in a lab environment, you may choose to make the Setup user account a Full Administrator during installation on the Identity Providers page in 1E Setup. This will help minimize the number of users required for an evaluation and reduce the initial configuration required.
If the Setup user account was not elevated during setup then it will only have limited access and as this is a system principal user the permissions are locked down by default. You can allow it to assume the Full Administrator role using the following steps:
Add an Azure Active Directory group to 1E permissions
Apply the 1E Full Administrator role to this group.
Add the Setup user account to the same Azure Active Directory group.
In the short term, it's fine to make use of full administrators in this way, but this practice is not really suitable for large-scale deployments and should be used with care for the following reasons:
The Full Administrator role has permission to do everything in 1E. It has across-the-board permissions to all Instruction Sets and therefore can be used to run actions that can have a major impact on your network.
The Full Administrator accounts receive emails for all the transactions that are performed by 1E.
Different approaches for defining permissions
1E provides a flexible system for defining permissions for the features. There are a number of different ways of approaching the task, here we outline the general choices that can be made for assigning 1E users to system and custom roles.
Managing access primarily using the Tachyon Permissions console
In this approach, Tachyon users are added individually using their Active Directory credentials. This approach is more secure than alternatives because all users, roles, and access rights are managed only through the Tachyon Permissions console.
Managing access using Active Directory
Using this approach, Tachyon users are added as Active Directory security groups. Tachyon roles are then associated with those groups, and management of the individual users who can access Tachyon is subsequently done only through Active Directory. There are broadly three options when using this approach:
A one-to-one approach where you create a Tachyon-specific role-based Active Directory group for each Tachyon role. For example, you could create a TCNGApprovers Active Directory security group, and add that group as a user in Tachyon, and then assign the All Instructions Approver role to the user.
A many-to-one approach, where you use one or more of your existing role-based Active Directory groups for each Tachyon role. For example, you could use the Active Directory groups for your desktop and help desk teams, create a Tachyon user for each group, and then assign the Tachyon role to all those Tachyon users.
A mixture of the above
Note
It is possible for an Active Directory user to be associated with roles for both running and approving actions. In practice, this is safe because Tachyon prevents users from being able to directly approve their own actions regardless of the roles they have been assigned.
Defining a custom Instruction set 1E role
If you want to base your 1E permissions around access to specific Instruction sets, you will need to create custom 1E roles. The Custom roles section lists built-in custom roles used by 1E Applications.
To create a custom role:
Navigate to the Settings→Permissions→Roles page.
Click the Add button to start the add role process.
In the New Role page subsequently displayed set the Name and Description.
With the Instruction Sets tab selected, select your required Instruction Sets from the list.
Set the Instruction set access rights by checking the required Actioner, Approver, Questioner and Viewer checkboxes.
When the associated rights have been set click Save to save your changes and automatically return to the Roles page.
You can now add assignments of users and groups and management groups to the new custom role by clicking the link in the Assignments column.
Click the + (plus icon) to add a new item and, from the Users and Groups drop-down menu either search for, or select the users or groups you want to associate the role with.
From the Management Group drop-down menu either search for, or select the management group you want to associate the role with. This can either be the built-in All Devices or a management group you have created in Settings→Permissions→Management groups.
Click the Save button to associate the selected options with the custom role.
The following rights can be set for an Instruction set, these relate to the primary operator roles of the 1E system:
Right | Description |
|---|---|
Actioner | Able to run actions defined in the Instruction Set. |
Approver | Able to approve actions defined in the Instruction Set for anyone other than self. If email is enabled, will receive an approval request email for each requested action in the Instruction Set. |
Questioner | Able to ask questions defined in the Instruction Set. |
Viewer | Able to view responses to questions run from the Instruction Set. |
Note
For details about how to load Instruction Definitions into 1E and then create, populate and delete Instruction sets, refer to the Instructions Menu page.