Communication Ports
Diagrams and tables with all the external Tachyon communication ports. Useful, if needed, for network and device firewalls.
Please refer to Tachyon Architecture for architecture diagrams.
Connections diagram
The diagram shows connections for Tachyon and its applications. It includes connections from clients and administration workstations, and outgoing connections to inventory sources, and to Microsoft Endpoint Configuration Manager that is optionally used by some applications.
It does not show connections for WakeUp, NightWatchman Enterprise, or Shopping, which have their own back-end servers. Their connection diagrams can be found in their documentation.
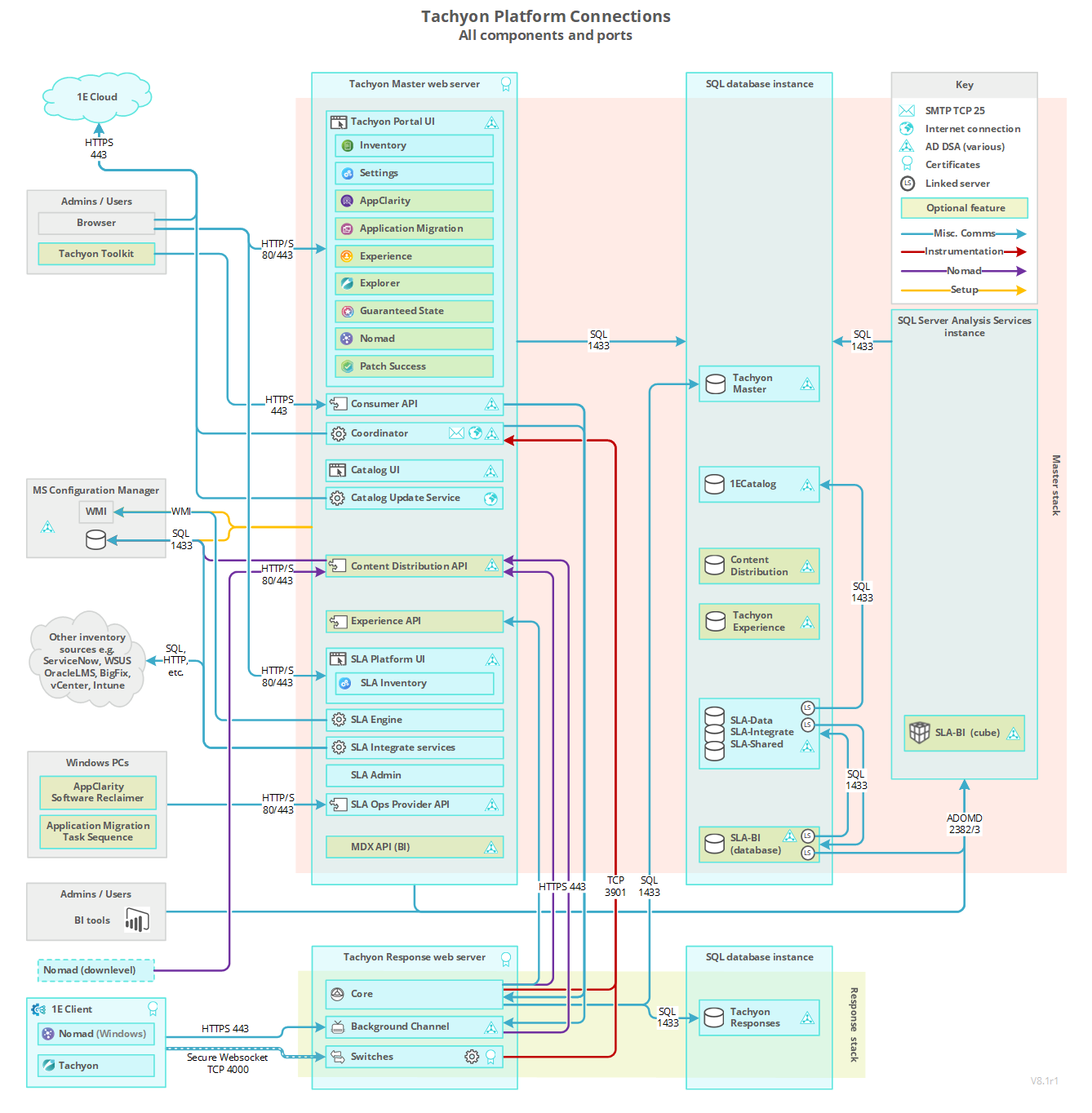
Firewall requirements for a Single-Server
The following table lists firewall requirements for a single-server where Tachyon Master Stack and Response Stack are installed on the same server. The table assumes a remote SQL Server hosting TachyonMaster and TachyonResponses databases. Each Tachyon component described in the table has at least one output and/or input. For each Tachyon component with output, there is a matching input.
Firewalls normally protect against incoming traffic from remote devices, however, the table below also includes outgoing connections. The table does not include internal communications within the Server.
In addition to but not included in the table are various ports that Tachyon uses to communicate with Microsoft services, including Certificate Services and Active Directory. The Coordinator Workflow service queries AD for email details; the Consumer API queries AD for security details.
Port requirements are not provided here for Nomad, Shopping and WakeUp modules of the 1E Client. Only the ports used by the client feature of the 1E Client are listed.
If Nomad is being used by the client on Windows computers, it has additional port requirements of its own, which are not changed by Tachyon.
Additional ports may be required if Tachyon instructions need to connect to non-Tachyon content sources.
There may be additional requirements if the environment has had default security settings changed.
Tachyon Servers
Device | Port | Protocol | Direction | Usage | Configurable |
|---|---|---|---|---|---|
TCP 443 | HTTPS | Incoming |
| Yes, during installation. In the Website Configuration panel in Tachyon Setup. See HTTPSIISPORT. Setup installs other components using the same settings as Tachyon Server. | |
TCP 80 | HTTP | Incoming |
| Yes, during installation. In the Website Configuration panel in Tachyon Setup. See HTTPSIISPORT. Tachyon Setup installs other components using the same settings as Tachyon Server. | |
TCP 443 | HTTPS | Incoming |
| Yes, during installation. In the Website Configuration panel in Tachyon Setup. See HTTPSIISPORT. | |
TCP 443 | HTTPS | Outgoing |
| The port used to connect to the 1E Cloud Services is not configurable. | |
TCP 6002 | WebSocket (ws) | Incoming Outgoing |
| Yes, configurable after installation. NoteIntegrate Agent component is not shown on the diagram, and installation on remote systems is not supported. | |
TCP 4000 | WebSocketSecure (wss) | Incoming |
| Switch ports are not configurable using the Server installer. A Switch port can be changed post-installation, by configuring the value in the Port column for the relevant Switch in the SwitchConfiguration table in the Tachyon Master database. If the Switch port is changed after deploying 1E Client (with Tachyon features enabled) then the corresponding Switch port must be updated in each Client's configuration file. Clients initiate and maintain a WebSocket Secure connection to a Switch, which the Switch uses to communicate back to the clients. | |
TCP 25 | SMTP | Outgoing |
| Yes. In this version of Tachyon, SMTP Authentication is not configurable using the Server installer. The default is anonymous authentication. However, it can be changed post-installation. For details of changing the SMTP configuration and disabling email notifications, please refer to Changing the SMTP Host configuration. | |
TCP 1433 | TDS | Outgoing |
| Not configurable from Setup. In the Database Servers panel in Tachyon Setup you can select a SQL Server instance. The instance can be installed using a non-standard port. However, selecting an instance that uses a non-standard port will not change the port used by the Tachyon Installer, and installation will fail. If you require the use of a non-standard port on a Default SQL Server instance, contact 1E for guidance on a manual workaround. If using a Named Instance that is set to its default configuration where the server automatically chooses a random port (or if you manually configured the instance to use a fixed port), then the SQL Browser service needs to be enabled to let the Tachyon Server determine the port in use. You will need to open UDP port 1434 used by the SQL Browser. See SQLSERVER_MASTER. | |
TCP 1433 | TDS | Outgoing |
| Configurable in various Connectors, please refer to Connectors page. | |
TCP 135 and 445 (initially) | WMI (DCOM) | Outgoing |
| Not configurable. Please refer to Provider configuration page and Nomad. | |
TCP 1433 | TDS | Outgoing |
| Not configurable from Setup. See the comments above for the Tachyon Server (Master Stack). See SQLSERVER_RESPONSES. | |
TCP 1433 | TDS | Incoming |
| Not configurable from Setup. See the comments above for the Tachyon Server (Master Stack). See SQLSERVER_MASTER. | |
TCP 1433 | TDS | Incoming |
| Not configurable from Setup. See the comments above for the Tachyon Server (Master Stack). See SQLSERVER_RESPONSES. |
Tachyon clients
Device | Port | Protocol | Direction | Usage | Configurable |
|---|---|---|---|---|---|
TCP 4000 | WebSocket Secure (wss) | Outgoing |
| Yes. See Tachyon client settings. Switch=<SwitchName>:<SwitchPort> Anything other than port 4000 requires a Tachyon Server with a Switch using the same port number. Clients initiate and maintain a WebSocket Secure connection to a Switch, which the Switch uses to communicate back to the client. | |
TCP 443 | HTTPS | Outgoing |
| Yes, during installation. See Tachyon client settings. BackgroundChannelUrl=https:/<1EplatformFQDN>:<port>/Background | |
Clients | TCP 7766 | HTTPS | Outgoing and Incoming |
| Yes, during installation. See Tachyon client settings. MODELE.INTERACTION.PORT=<port> |
TCP 443 | HTTPS | Outgoing |
| Anything other than port 443 requires the port number to be included in the browser URL when connecting to the Tachyon portal, API or SLA Platform UI. | |
TCP 80 | HTTP | Outgoing |
| Anything other than port 80 requires the port number to be included in the browser URL when connecting to the 1E Catalog UI. |
Firewall requirements for a remote Catalog Web Server
The following table lists firewall requirements when the Catalog Web Server is on a different server than the Tachyon Server. This can happen if Tachyon Server is installed in an environment that already has a 1E Catalog server installed to support Application Migration or AppClarity.
Device | Port | Protocol | Direction | Usage | Configurable |
|---|---|---|---|---|---|
Tachyon Server (Master Stack) | TCP 80 | HTTP | Outgoing |
| Yes, requires manual configuration of Tachyon Server if not using default port 80. |
Catalog Server | TCP 80 | HTTP | Incoming |
| Yes, during installation. See 1E Catalog installer properties. |
Catalog Server | TCP 443 | HTTPS | Outgoing |
| The port used to connect to the 1E Cloud Services is not configurable. |
Catalog Server | TCP 1433 | TDS | Outgoing |
| Yes, during installation. See 1E Catalog installer properties. |
SQL Server(1E Catalog database) | TCP 1433 | TDS | Incoming |
| Yes, during configuration of the SQL Server instance. |
Browsers | TCP 80 | HTTP | Outgoing |
| Yes, during installation. See 1E Catalog installer properties. |
Firewall requirements for a remote Tachyon Response Stack
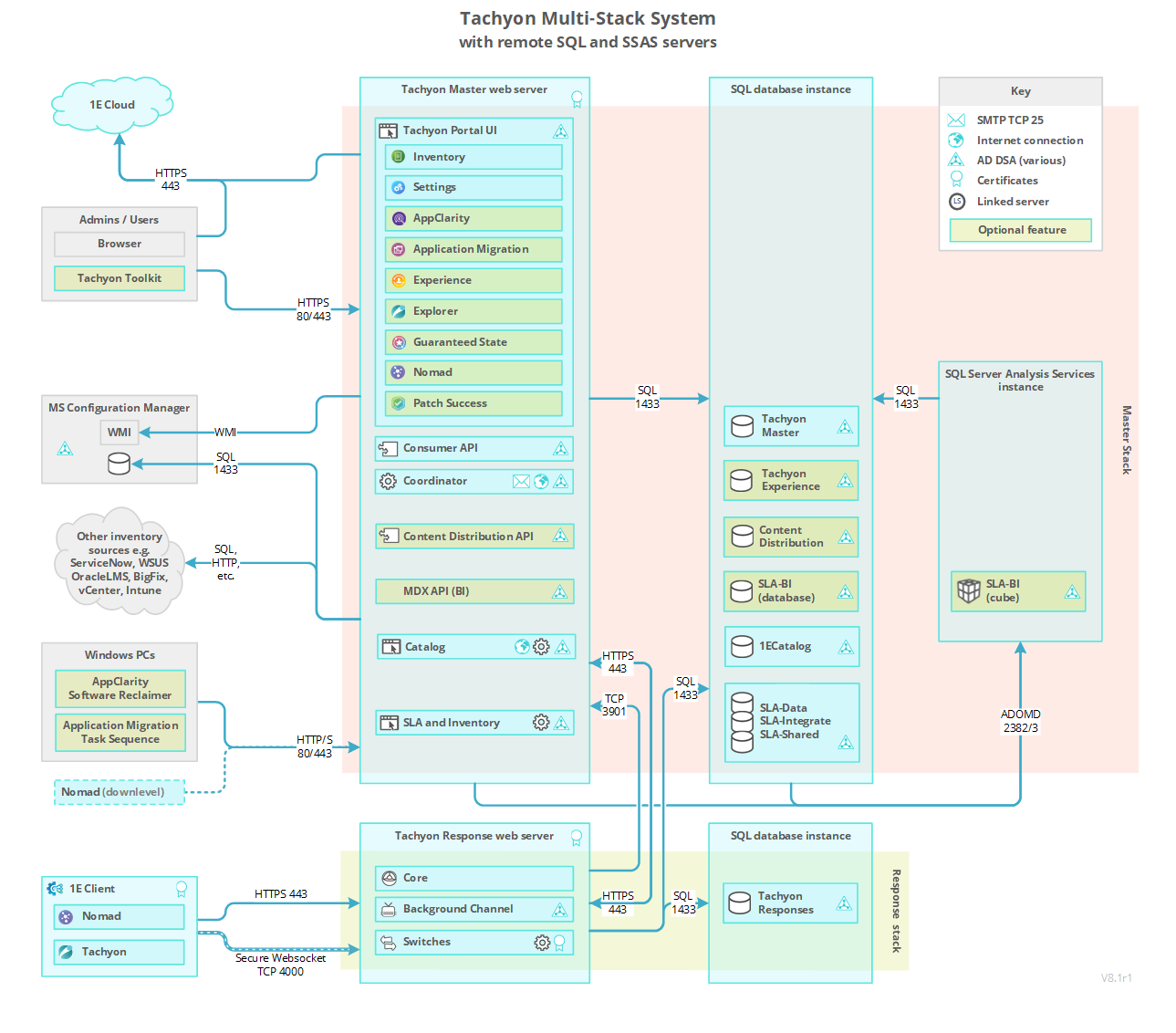
The following table lists firewall requirements when using a Tachyon Response Stack that is remote from the Tachyon Master Stack, which is additional to the ports required for a Single-Server. Each Tachyon component described in the table has at least one output and/or input. For each Tachyon component with an output, there is a matching input.
Device | Port | Protocol | Direction | Usage | Configurable |
|---|---|---|---|---|---|
Tachyon Server (Master Stack) | TCP 443 | HTTPS | Outgoing |
| Yes, during the installation of the Response Stack. In the Website Configuration panel in Tachyon Setup. See Server installer property HTTPSIISPORT, refer to Tachyon Server installer properties. The Consumer API connection to the Core is only used for remote Response Stacks. |
Tachyon Server (Response Stack) | TCP 443 | HTTPS | Incoming |
| Yes, during the installation of the Response Stack. In the Website Configuration panel in Tachyon Setup. See Server installer property HTTPSIISPORT refer to Tachyon Server installer properties. The Consumer API connection to the Core is only used for remote Response Stacks. |
Tachyon Server (Master Stack) | TCP 3901 | WebSocket (ws) | Incoming |
| Yes, but please contact 1E for advice. |
Tachyon Server (Response Stack) | TCP 3901 | WebSocket (ws) | Outgoing |
| Yes, but please contact 1E for advice. |
SQL Server (TachyonMaster database) | TCP 1433 | TDS | Incoming |
| Not configurable from Setup. In the Database Servers panel in Tachyon Setup you can select a SQL Server instance. The instance can be installed using a non-standard port. However, selecting an instance that uses a non-standard port will not change the port used by the Tachyon Installer, and installation will fail. If you require the use of a non-standard port on a Default SQL Server instance, contact 1E for guidance on a manual workaround. If using a Named Instance that is set to its default configuration where the server automatically chooses a random port (or if you manually configured the instance to use a fixed port), then the SQL Browser service needs to be enabled to let the Tachyon Server determine the port in use. You will need to open UDP port 1434 used by the SQL Browser. See Server installer property, SQLSERVER_MASTER, refer to Tachyon Server installer properties. |
Tachyon Server (Response Stack) | TCP 1433 | TDS | Outgoing |
| Not configurable from Setup. See the comments above for SQL Server (TachyonMaster database). See Server installer property SQLSERVER_MASTER, refer to Tachyon Server installer properties. |
Firewall requirements for a Tachyon DMZ Server
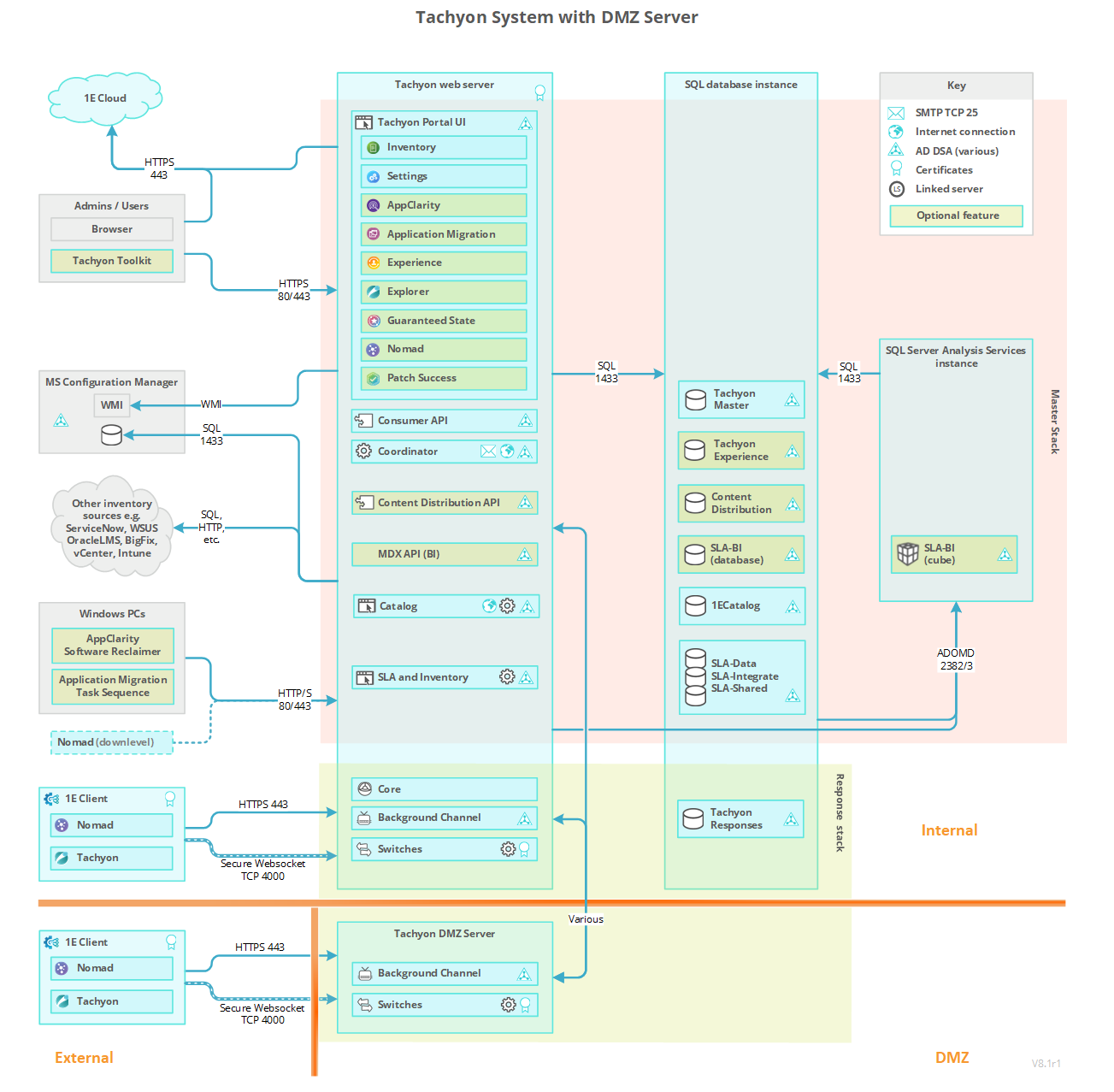
The following table lists the subset of ports needed when hosting Tachyon Switch and Background Channel components on a DMZ Server to support devices external to the network. Each Tachyon component described in the table has at least one output and/or input. For each Tachyon component with an output there is a matching input.
Note
If the server is a domain joined server it needs to be able to access Microsoft services, including Certificate Services and Active Directory. If the server is not domain joined (a workgroup server) you will need to manually install its Web Server certificate.
In both cases you will also need to ensure that the server is able to validate the certificate, including accessing the certificate's remote CRL Distribution Point.
The following table does not cover port requirements when using ADFS and SAML tokens to authenticate clients. In this documentation we just provide details of the simplest option, which uses certificates for client authentication. For details of how to configure Tachyon to support the more complex implementations, please contact 1E.
Device | Port | Protocol | Direction | Usage | Configurable |
|---|---|---|---|---|---|
DMZ Server | TCP 443 | HTTPS | Incoming |
| Yes, during installation. In the Website Configuration panel in Tachyon Setup. See Server installer property HTTPSIISPORT, refer to Tachyon Server installer properties. |
DMZ Server | TCP 443 | HTTPS | Outgoing |
| Yes, during installation. In the Website Configuration panel in Tachyon Setup. See Server installer property HTTPSIISPORT, refer to Tachyon Server installer properties. |
DMZ Server | TCP 3901 | WebSocket (ws) | Outgoing |
| Yes, but please contact 1E for advice. |
DMZ Server | TCP 400n | TCP | Incoming |
| If the value for the Switch port has been changed, the port you need to open should be the Switch client port + 1. For example, if a Switch client port is 4000 then Switch poke port is 4001. |
DMZ Server | TCP 4000 | WebSocket Secure (wss) | Incoming |
| Switch client ports are not configurable using the Server installer. A Switch client port can be changed post-installation, by configuring the value in the Port column for the relevant Switch in the SwitchConfiguration table in the Tachyon Master database. Clients initiate and maintain a WebSocket Secure connection to a Switch, which the Switch uses to communicate back to the client. |
DMZ Server | TCP 80 | HTTP | Outgoing |
| |
Tachyon Server (Response Stack) | TCP 443 | HTTPS | Incoming |
| Yes, during installation. In the Website Configuration panel in Tachyon Setup. See Server installer property HTTPSIISPORT, refer to Tachyon Server installer properties. |
Tachyon Server (Master Stack) | TCP 443 | HTTPS | Outgoing |
| Yes, during installation. In the Website Configuration panel in Tachyon Setup. See Server installer property HTTPSIISPORT, refer to Tachyon Server installer properties. |
Tachyon Server (Response Stack) | TCP | TCP | Outgoing |
| Switch client ports are not configurable using the Server installer. A Switch client port can be changed post-installation, by configuring the value in the Port column for the relevant Switch in the SwitchConfiguration table in the Tachyon Master database. If the value for the Switch client port has been changed the port you need to open should be the Switch client port + 1. For example, if Switch client port is 4000 then Switch poke port is 4001. |
Tachyon Server (Master Stack) | TCP 3901 | WebSocket (ws) | Incoming |
| Yes, but please contact 1E for advice. |
Internet-facing clients | TCP 443 | HTTPS | Outgoing |
| Yes, during installation. See Tachyon client settings. |
Internet-facing clients | TCP 4000 | WebSocket Secure (wss) | Outgoing |
| Yes. See Tachyon client settings. There must be a matching Switch using the same port. Clients initiate and maintain a WebSocket Secure connection to a Switch, which the Switch uses to communicate back to the client. |
Internal Server communications
The following is a list of ports used within the Tachyon Platform, and not listed in the Single-Server table above, and as such should not affect firewall requirements. Some of these are listed in the DMZ table above.
Port | Protocol | Usage | Configurable | ||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|
TCP 3900 | WebSocket (ws) |
| Yes, post-installation, but not recommended. Contact 1E for advice. The following may be configured during installation.
| ||||||||
TCP 3901 | WebSocket (ws) |
| |||||||||
TCP | TCP |
| |||||||||
TCP 443 | HTTPS |
| |||||||||
TCP 80 | HTTP |
| |||||||||
TCP 8081 | HTTPS |
| |||||||||
TCP 6002 | HTTP |
|